
Trend Micro - Legacy radio frequency technology for industrial applications can be abused through five classes of attacks that we've identified. The attacks can have consequences such as sabotage, theft, and extortion.

Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News
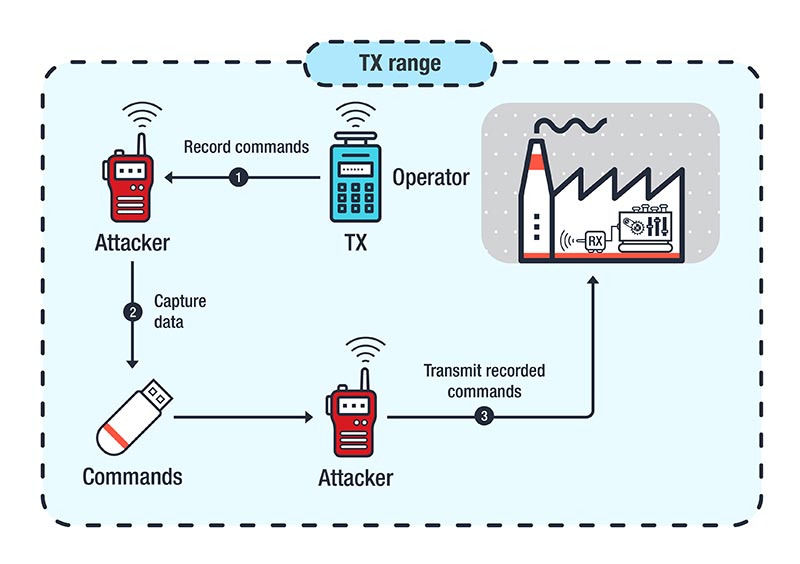
Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News

Wireless coexistence – New attack technique exploits Bluetooth, WiFi performance features for 'inter-chip privilege escalation' | The Daily Swig






_637280703542341277.png)










